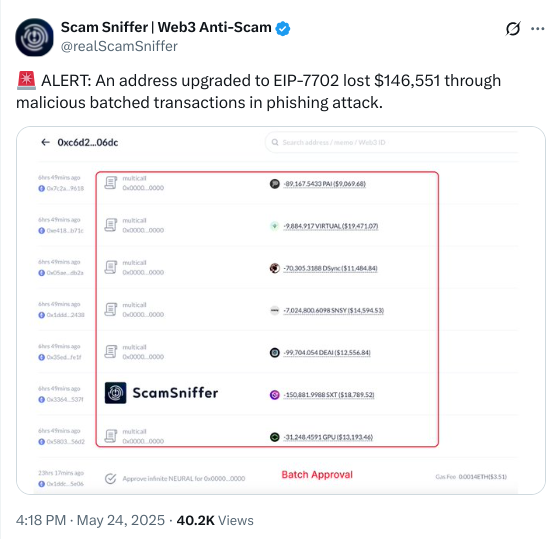
On May 24, 2025, Inferno Drainer utilized Ethereum’s EIP-7702 to steal $150,000 from various crypto wallets via phishing. The attack is an indication of the substantial advancement of phishing attacks in which the hackers have been utilizing advanced aspects of the Ethereum network.
How the Inferno Drainer Attack Worked
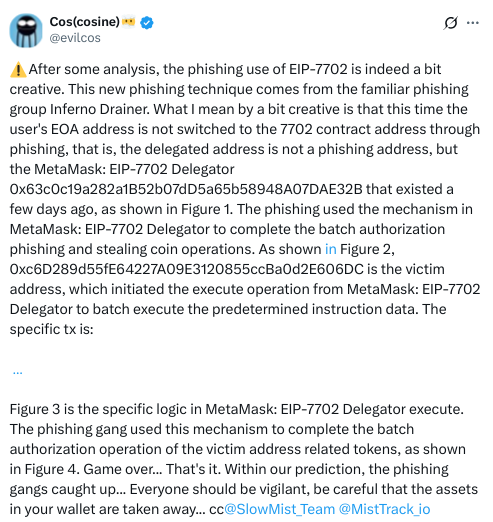
Inferno Drainer used a delegated MetaMask wallet that complied with EIP-7702. Ethereum upgrade allows externally owned accounts (EOAs) to impersonate smart contracts for a temporary period.
Furthermore, since batch authorizations are supported, attackers signed token transfers without their victims’ knowledge. Victims unknowingly triggered an “execute” operation on MetaMask, and MetaMask quietly executed malicious data in the background, SlowMist CEO Yu Xian explained.
Consequently, this attack demonstrates phishing methods enhancing from typical wallet thefts to more advanced strategies. Xian described, “The phishing group use this mechanism to perform batch authorization operations on tokens of the victim’s address.”
Growing Crypto Security Threats
This is among the bigger trends within the world of cryptocurrency. In the last month alone, attackers stole more than $5 million from over 7,500 individuals through these phishing attempts. These kinds of incidents remind users to be careful to safeguard their digital fortune. What experts recommend in the future is to check token permissions on a frequent basis and watch for any suspicious delegations as it pertains to EIP-7702.
Additionally, Scam Sniffer, a web3 anti-scam platform, encourages users to check a website prior to login or approval of transactions. Community members must regularly update their token permissions and avoid clicking suspicious links.
The Path Forward
With more sophisticated phishing techniques, there is a need for the crypto market to enhance campaigns that inform consumers about security features. Security specialists and social media influencers already offer advice that will help consumers spot and reject phishing attacks. The move is crucial in generating awareness in an increasingly sophisticated world.
Ultimately, future crypto security will rely on collaboration between security experts, users, and programmers. By creating a mindset of awareness and embracing state-of-the-art defensive practices, the crypto community can respond adequately to these new forms of attacks.
As a result, users will have to get cautious and careful in their security practices as a measure to protect their assets. Token authorization verifications and prudent transactional behaviors daily are crucial in handling these new threats. Moreover, staying informed about the latest security threats will empower users to navigate the complexities of the crypto landscape safely.
















